Whatsapp How to Know if Read in Group
WhatsApp's End to End Encryption, How does it work?
You must take heard about WhatsApp using finish to end encryption.
What is it?
In layman'southward words, every message that you sent to your friend, is encrypted on your device, this encrypted message passes through network and a whole bunch of servers, reaches your friend'southward device, and finally, it is decrypted on friend's device. And then every bit long as underlying cryptography is intact, you can be bodacious that no one else other than your friend knows nigh your dirty piffling underground.
Is information technology every bit simple as information technology sounds?
No. Purpose of this mail is to give you lot the sneak peek of what is actually happening behind the scene.
Features of a secure messaging system
So what possible features such system should take? I will introduce a few characters in the system. I will choose Ankita, Bud, and Mayank. (Cryptography literature uses Alice, Bob, and Mallory. The names are chosen based on their roles). Ankita and Bud desire to exchange letters. Mayank is evil, and he wants to listen on the chat betwixt Ankita and Bud, and mayhap desire to send messages to Ankita interim as Bud and to Bud acting every bit Ankita. We desire our system to have the post-obit properties:
- Confidentiality: Mayank can't know what messages Ankita and Bud ship to each other.
- Integrity: If Bud receives a message from Ankita, He can check if the message was modified by Mayank on the mode.
- Authenticity: When Bud receives a message from Ankita, He tin be sure it is from Ankita and not from Mayank.
Another feature that we might want is deniability, i.eastward., if someone recovers Ankita'due south or Bob's former messages in futurity, it can't be linked to them and they tin deny having sent that message.
(ane) could exist accomplished using encryption/decryption mechanism. (2) and (3) could be achieved through MACs and Digital Signatures. These primitives require secure substitution of some underground (In case of Symmetric Key Cryptography ) or establishment of each other's public information (case of Public Fundamental Cryptography ). Public Key Cryptography is prissy in the sense that you don't demand to share a hush-hush with someone you want to send a message to, as long you know each other's public primal or (identity). Problem with that arroyo is that Ankita needs to be assured that she actually has Bud's public key and it is not of Mayank'southward and so She can securely communicate with Bud by encrypting the messages with Bud'southward public key. Simply Bud, who has the corresponding private key can decrypt the message. Similarly, In the example of symmetric fundamental cryptography, Mayank and Ankita need a mechanism to share the secret (Perchance meet in person and exchange), which they will use for encryption/decryption. In the former case, it is okay if Mayank learns nearly Ankita and Bud's public key (It's Public).
WhatsApp'south E2E Encryption protocol
WhatsApp uses open source Signal Protocol developed past Open up Whisper Systems (They take their own messaging awarding, Point). Signal Protocol uses primitives like Double Ratchet Algorithm, prekeys, Triple Diffie Hellman, Curve25519, AES and HMAC_SHA256.
I will summarize these primitive before putting them all together to empathize Signal Protocol.
Agreement Primitives
Prekeys
These are Curve25519 key pairs generated on device during install fourth dimension. There is 1 Signed Prekey Pair and several i time prekey pairs. The Identity Public primal and the Public keys of the prekey pairs are signed by a long term Identity Undercover Key(Curve25519 private central correspond to Identity public central) and sent to the server during registration. Server stores these keys along with Identity Public key.
Curve25519
Elliptic curve used as office of Diffie Hellman Primal Exchange Protocol. I will discuss Elliptic Bend Cryptography in carve up post. Its security is based on difficulty of discrete logarithm problem in large finite groups.
Diffie Hellman Primal Agreement
Diffie Hellman Cardinal Agreement or Triple Diffie Hellman Handshake allows 2 parties to agree on a shared undercover over public channel (Mayank is able to mind to message exchanged by Ankita and Bud). It is based on modulo arithmetic big prime p and it basically works as follows,
0. Ankita and Bud agree on protocol parameters, large prime p and generator g. grand is the generator of multiplicative grouping modulo p. Generator is between 1 and p-1 and has this prissy property, that every chemical element in [ane, p] can be represented every bit g^one thousand mod p where k is in [0,p-2].
i. Ankita selects a random number ten between 1 and p-1 , her private key.
2. Bud selects a random number y between 1 and p-i, his private key.
3. Ankita sends Bud, x_p = yard^10 modernistic p , her public key.
four. Bud sends Ankita y_p = yard^y modern p, his public primal.
v. Ankita computes ss_a = y_p^x mod p.
half-dozen. Bud computes ss_b = x_p^y mod p.
After completion of protocol Ankita and Bud have a shared undercover ss_a = ss_b = g^(xy) mod p.
Mayank on the network sees x_p and y_p, and it is computationally infeasible for him to make up one's mind shared surreptitious without noesis of x or y.
We assume here that Mayank only come across the messages on channel between Bud and Ankita but doesn't tamper them.
Extended Triple Diffie Hellman Fundamental Agreement (X3DH)
X3DH is an extension of diffie hellman protocol for asynchronous setting. Imagine Ankita wants to establish a shared key with Bud to send the encrypted bulletin to him. In a higher place agreement works smoothly when Bud is online.
What if Bud is offline?.
She would have to wait for Bob to come online.
Likewise, In the in a higher place key agreement, Ankita and Bud accept no way to determine if they are talking to each other. They may exist both talking to Mayank (Man-in-the-middle) thinking they are talking to each other. The protocol might end up as Ankita and Mayank sharing a secret, Mayank and Bud like-minded on a key.
X3DH solves both these problems using a trusted third party and Prekeys. Ankita and Bud register signed prekeys (Signed using their long-term individual keys) on a trusted server. Each time one of them one wants to establish a shared cloak-and-dagger with other, the quondam fetches the signed prekey bundle of latter. Let'due south assume Ankita is the sender.
Now, Ankita does her office, performs DH Functioning (raising a public key with a private key, operation 5 in DH Agreement) iii or 4 times (depending on the prekeys she fetched from server). These operations are between,
- Ankita'southward long term private key(IKa) and Bud'southward signed prekey(SPKb).
- Ankita's ephemeral individual key(Eka) (from key pair generated specifically for this exchnage and deleted after) and Bud's signed prekey(SPKb).
- Ankita's ephemeral private cardinal (EKa) and Bud's long term public key(IKb).
- (if prekey bundle has a 1 time public key) Ankita'due south ephemeral private key(EKa) and Bud'due south Once public key(OPKb).
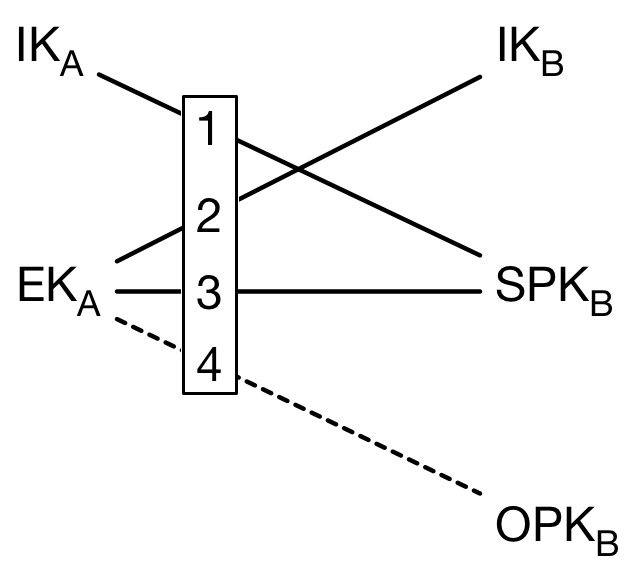
The outputs from the above steps are combined used as a central textile i.e. master cloak-and-dagger. These keys derived from master secret are used in Double Ratchet described below to ship subsequent encrypted messages to Bud, all of them include Ankita's imperceptible public cardinal, long-term identity key, and information on which of Bud'southward one fourth dimension public key is used ( in case it is in step four.)are included in header (plaintext). This ends x3dh from Ankita's side. The messages sent can be received by Bud if he is online or tin can exist stored on the server where Bud can fetch it later. When Bud receives the messages later, he can derive the same master surreptitious by using his private keys and Ankita'due south public keys in the message header.
This scheme allows Ankita and Bud to authenticate each other and derive shared secret to be used every bit a key material.
HMAC_SHA256
Information technology is keyed cryptographic hash role. Apart from the value to be hashed, this part also takes input a primal. Unlike hash function which is easy to compute for a given input, keyed hash office require knowledge of the cardinal. Hither it is used equally a key derivation role and MAC.
Double Ratchet
Ratchet is the name of a device that moves only in one management. Double Ratchet uses two cryptographic Ratchets, i.e., deriving new keys from electric current keys and moving frontwards, while forgetting old keys. The two Ratchets used are Diffie-Hellman ratchet and Hashing ratchet. Each fourth dimension a Diffie Hellman ratchet movement frontwards, a clandestine is established between sender and receiver using Diffie Hellman described above, and the surreptitious is used to derive two new keys (root key and concatenation cardinal). Hashing Ratchet moves forward by using a Key Derivation Function using chain primal to generate a message central to encrypt a bulletin to be sent, and a chain central to be used for the next ratchet move. This Ratcheting provides a useful property to a protocol known as forrard secrecy, i.e., if Ankita or Bud comprise their keys in futurity, their previous messages cant be comprised (decrypted), as long as ratchet works as expected (old keys are deleted).
Putting Everything Together
I take attempted to summarize the primitives used in the protocol which could exist difficult to digest all at one time. Bold the primitives work equally expected, following steps volition describe the working of protocol in much simpler language. These steps occur when Ankita wants to transport a message to Bud using WhatsApp:
- Registration of Clients with whatsapp server (Mobile apps on Ankita's and Bud'due south telephone). It includes registering signed prekeys.
On Ankita's Side
- Session setup by Ankita using x3dh.
- In footstep two, Ankita calculates principal hugger-mugger and Using DH Ratchet step, derives a root key and a chain key to be used by Hashing Ratchet.
- Ankita derives a message key and adjacent chain cardinal using the chain key using Hashing Ratchet.
- She encrypts her message using bulletin cardinal ( AES256 in CBC way ).
- Every time she sends a message her Hashing Ratchet moves forrard.
- Every time she receives a response from Bud, which includes a new public central in header, she advances her DH Ratchet, calculates a new root cardinal and a new chain key.
On Bud'southward Side
- When he retrieves showtime bulletin from Ankita, he completes the session setup by deriving the master secret, root cardinal, chain key and the message key.
- Uses messages central to decrypt.
- If he wants to send message, he generates a new ephemeral fundamental pair, moves his DH ratchet frontwards using the root central and ephemeral private key and replaces his concatenation key and message cardinal.
- New message key is derived from chain cardinal and message is encrypted.
- Encrypted message is sent with Bud'due south ephemeral key in header.
In the image below (Bold information technology'south Ankita's Telephone), message in white boxes are ones received and greenish ones are the messages sent. Each pair of continuous boxes tin help you visualize ratchet movements.
- White -> White: Hashing Ratchet of Bud moves forward by 1 step (new message central and next chain keys are derived).
- Dark-green -> Green: Hashing Ratchet of Ankita moves forward by i step (she derives new message cardinal and chain primal).
- White -> Green: Ankita's DH Ratchet moves forward by i step(she derives new root central and chain key)
- Dark-green -> White: Bud's DH Ratchet moves 1 step forwards (He derives new root central and concatenation cardinal)
Media Attachements and Files
Media files are encrypted and uploaded to the blob store. When Ankita sends an epitome or video to Bud, the pointer to the location of encrypted image or video file in blob store is encrypted and sent using to a higher place pairwise scheme.
Grouping Messages
- Whenever a group fellow member sends his/her 1st bulletin, he/she generates a sender key which is distributed to all grouping members using one-to-1 protocol described to a higher place.
- For subsequent letters, messages are encrypted using new message cardinal derived by Hashing Ratchet (this is different from the one used in i-to-i).
- Since each fellow member has every other member's sender key, they can motion, ratchet corresponding to the sender to decrypt the message.
- Whenever a fellow member leaves the group, sender keys are renegotiated (step i).
Calling
Calling is synchronous/real-time. Whenever Ankita calls bud, she generates a random SRTP cloak-and-dagger.
This secret is sent to Bud using the pairwise system. If he responds to phone call, the encrypted session begins.
Miscellaneous
Apart from the end to end encryption, the the channel between the whatsApp customer and whatsApp server is secure. Plaintext Headers are not visible to anyone listing on channels. This is server'south extra wrapping over Ankita's already wrapped gift(bulletin) to Bud.
Wrapping Up
And then yous might take wondered at some point, based on an ad you saw or possibly a whatsApp forward, that whatsApp is probably reading your messages, Every bit yous sometimes happen to see ads of things on your facebook feed which y'all happen to hash out on whatsapp chats. Lets uncover some possibilities and conspiracy theories.
- If y'all trust that whatsApp's end to end encryption is actually implemented equally per signal specification, so no way they are able to read your chats. Unlike Signal application, whatsApp'southward code is not open source then you tin can't really ostend.
- Assuming signal protocol is implemented correctly, whatsApp servers still know which whatsApp user is interacting with which user, how ofttimes, how recently. Same is true for signal app's servers. (It's a difficult trouble to solve). If you lot take your mobile number registered on facebook and is the same ane you apply for whatsApp. They could (hypothetically) utilize this information to associate your friend's activity on facebook and serve you relevant ad which ends up surprising yous.
- They might take enough data from other channels and such an advertising is merely an coincidence of their actually expert advertisement serving algorithms.
References
- Signal Developer Docs.
- Indicate Weblog posts.
- WhatsApp whitepaper.
- Diffie Hellman simple caption.
- Off the record messaging, OTR
Source: https://medium.com/@panghalamit/whatsapp-s-end-to-end-encryption-how-does-it-work-80020977caa0
0 Response to "Whatsapp How to Know if Read in Group"
Post a Comment